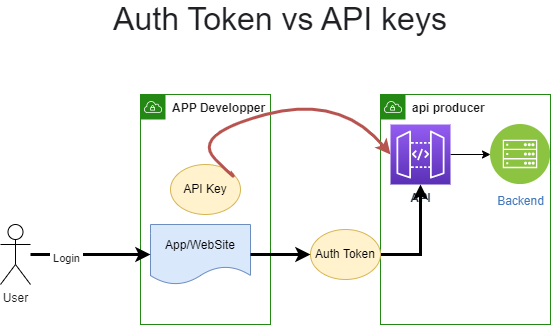
JWT (JSON Web Token) and API key are two different ways to authenticate requests made to an API (Application Programming Interface).
JWT is a type of token-based authentication that is used to securely transmit information between parties. It is commonly used to authenticate requests made to an API by sending the JWT in the HTTP Authorization header. The JWT consists of a header, payload, and signature, and is encoded in base64. The header and payload contain JSON objects that contain information about the JWT, such as the algorithm used to generate the signature and the claims (assertions about an entity). The signature is used to verify that the sender of the JWT is who it claims to be, and that the message wasn’t changed along the way.
API keys, on the other hand, are unique strings that are used to identify the client making the API request. They are often used to track and control the usage of an API, and to enable rate limiting. API keys are usually passed as a query parameter in the API request, or as an HTTP header.
Both JWT and API keys can be used to authenticate requests to an API, but they have some differences. JWT provides a more secure way to authenticate requests, as the information contained in the JWT is signed and verified, whereas API keys are simply strings that can be easily compromised if not properly protected. On the other hand, API keys are simpler to use and don’t require the overhead of generating and verifying signatures, and they can be easily rotated or revoked if necessary.
Implement API key authentication in a .NET Core project
To implement API key authentication in a .NET Core project, you can follow these steps:
- Generate an API key: First, you’ll need to generate an API key for each client that will be accessing your API. You can generate a unique API key using a secure random number generator or a hashing function. You should store the API key in a secure database, along with the client’s identity and any other relevant information.
- Add the API key to the request: The client should include the API key in every request to the API. You can pass the API key as a query parameter in the URL, or as an HTTP header.
- Validate the API key: In the API, you’ll need to validate the API key provided in the request. You can do this by looking up the API key in the database and verifying that it belongs to the correct client. If the API key is invalid or has been revoked, you can return an error response.
- Authorize the request: Once you’ve validated the API key, you can authorize the request based on the client’s identity and permissions. You can use .NET Core’s built-in authorization framework to implement this step.
public class Startup
{
public void ConfigureServices(IServiceCollection services)
{
// Add the API key validation handler to the pipeline
services.AddTransient<IApiKeyValidator, ApiKeyValidator>();
}
public void Configure(IApplicationBuilder app, IWebHostEnvironment env)
{
app.UseRouting();
app.Use(async (context, next) =>
{
// Validate the API key
var apiKey = context.Request.Headers[“Api-Key”].FirstOrDefault();
var validator = context.RequestServices.GetService<IApiKeyValidator>();
if (!validator.Validate(apiKey))
{
context.Response.StatusCode = (int)HttpStatusCode.Unauthorized;
return;
}
// API key is valid, so proceed with the request
await next();
});
app.UseEndpoints(endpoints =>
{
endpoints.MapControllers();
});
}
}
public class ApiKeyValidator : IApiKeyValidator
{
public bool Validate(string apiKey)
{
// Look up the API key in the database and return true if it’s valid
// Otherwise, return false
}
}
you can use API key authentication and Cognito in the same project.
Cognito is a service provided by AWS (Amazon Web Services) that provides user management and authentication capabilities for applications. You can use Cognito to authenticate users and manage their permissions and access to resources in your application.
API key authentication, on the other hand, is a way to authenticate API requests using a unique key that identifies the client making the request. API keys are often used to track and control the usage of an API, and to enable rate limiting.
You can use both API key authentication and Cognito in the same project by implementing them separately. For example, you can use API key authentication to authenticate API requests made by external clients, while using Cognito to authenticate users within your application. Alternatively, you can use API key authentication to authenticate API requests made by clients that are authenticated using Cognito.
It’s also possible to use both API key authentication and Cognito together in the same API request. For example, you could require that the API key be included in the request header, and also require that the user be authenticated using Cognito. In this case, you would need to validate both the API key and the user’s Cognito credentials before allowing the request to proceed.