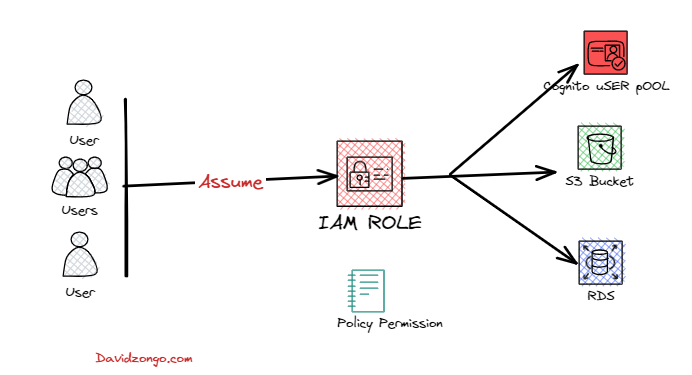
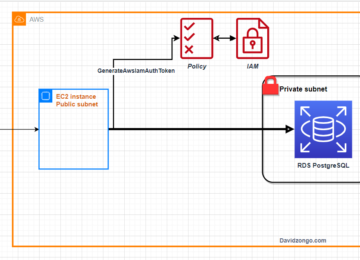
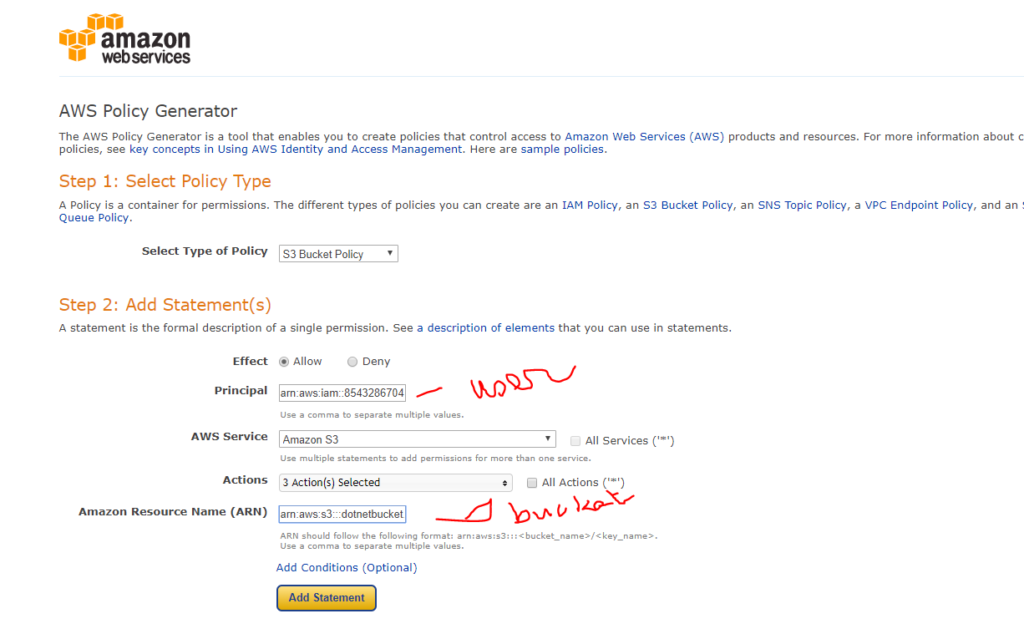
AWS Identity and Access Management (IAM) enables you to create and manage AWS users and groups, and define the permissions to access AWS resources. In this tutorial, we’ll show you how to create an IAM role that can be used by your .NET application to access AWS resources. We’ll assume you have basic knowledge of AWS IAM and .NET development.
Step 1: Create an IAM Role
- Open the IAM console and navigate to the Roles page.
- Click the Create Role button.
- Choose the Another AWS Account option and enter the account ID of your .NET application’s AWS account.
- Select the Allow programmatic access and AWS Management Console access options.
- Attach the AmazonCognitoPowerUser policy to the role. This policy provides permissions to perform administrative actions on Amazon Cognito user pools.
- Review the settings and click the Create Role button.
Step 2: Assume the IAM Role and Get Temporary Credentials
In your .NET application, use the AWS SDK for .NET to assume the IAM role and get temporary credentials.
Step 3: Configure the AWS SDK for .NET to Use the Temporary Credentials
Configure the AWS SDK for .NET to use the temporary credentials.
The full code on 1) and 2)
using Amazon.CognitoIdentityProvider;
using Amazon.CognitoIdentityProvider.Model;
using Amazon.Runtime;
using Amazon.SecurityToken;
using Amazon.SecurityToken.Model;
using System.Net;
namespace demoAppIAMRoleECS.Controllers
{
public class ClientController : Controller
{
// The ARN of the IAM role that has permission to create App clients
private const string ROLE_ARN = "arn:aws:iam::123456789012:role/YourRoleName";;
// The name of the AWS region where your Cognito User Pool is located
private const string REGION_NAME = "us-east-1";
// The name of your Cognito User Pool
private const string USER_POOL_ID = "us-east-1_HSIU0NS";//USER POOL
// The name of the App client you want to create
// private const string APP_CLIENT_NAME = "YourAppClientName";
public async Task<ActionResult> CreateAppClient(string? appClientName)
{
// Get temporary credentials using the IAM role
var stsClient = new AmazonSecurityTokenServiceClient();
var assumeRoleRequest = new AssumeRoleRequest
{
RoleArn = ROLE_ARN,
RoleSessionName = "MySessionName"
};
var assumeRoleResponse = await stsClient.AssumeRoleAsync(assumeRoleRequest);
var sessionCredentials = assumeRoleResponse.Credentials;
var tempCredentials = new SessionAWSCredentials(
sessionCredentials.AccessKeyId,
sessionCredentials.SecretAccessKey,
sessionCredentials.SessionToken);
// Create a CognitoIdentityProviderClient using the temporary credentials
var cognitoClient = new AmazonCognitoIdentityProviderClient(
tempCredentials,
RegionEndpoint.GetBySystemName(REGION_NAME));
//// Create the App client
var createAppClientRequest = new CreateUserPoolClientRequest
{
ClientName = appClientName,//APP_CLIENT_NAME,
UserPoolId = USER_POOL_ID,
GenerateSecret = true,
RefreshTokenValidity = 30,
//ReadAttributes = new[] { "email" },
//WriteAttributes = new[] { "email" },
PreventUserExistenceErrors = "ENABLED"
};
var createAppClientResponse = await cognitoClient.CreateUserPoolClientAsync(createAppClientRequest);
//// Get the client ID and secret from the response
var clientId = createAppClientResponse.UserPoolClient.ClientId;
var clientSecret = createAppClientResponse.UserPoolClient.ClientSecret;
// Display the client ID and secret in the view
ViewBag.ClientId = clientId;
ViewBag.ClientSecret = clientSecret;
return View();
}
}
}